Submitted by Rich on April 30, 2012 - 7:57pm
 This tip is something I have wanted to do for ages.
This tip is something I have wanted to do for ages.
Has anyone ever wanted to change the bootsplash to something a little more personal. Personally I don't like the color green and the pale green bootsplash that openSUSE uses looks more like the poop from a sick baby. Well its supper easy to change. I had no idea how easy it was until I did it.
Submitted by Rich on April 22, 2012 - 7:52pm
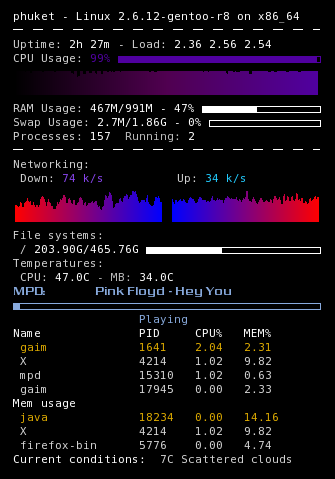 Just a new tip I figured out that I hope someone else will get some use out of.
Just a new tip I figured out that I hope someone else will get some use out of.
I use conky quite a bit on both my desktop and netbook. However, my netbook has limited desktop space so I wanted to hide some elements that where not needed like the eth0 info when I am on wifi. so this is what I did.
Submitted by Rich on April 20, 2012 - 12:45pm
I have spent 2 hours dealing with this and i finally have it working.
In opensuse 12.1 you need the root password to create a system connection in network manager. I didn't like this and wanted to be able to connect without a password so here is what i did.
Submitted by Rich on April 17, 2012 - 7:36pm
I have had a problem for a while now. I wanted to display my hard drive temp's in conky.
To do this I used this command.
This worked great except for the fact that the conky instance I was using has a .7 second update interval. This made my hard drive light blink constantly and because of where my case was it was quite annoying when watching a movie or something. So to solve this I created a script that I could run in cron that would write the info I needed out to a txt file in my temp directory.
Submitted by Rich on April 12, 2012 - 7:29pm
 I have a freenas box and I like to periodically check the smart status on my drives to make sure everything’s OK. I just figured out a really sweet way to do it without lifting a finger.
I have a freenas box and I like to periodically check the smart status on my drives to make sure everything’s OK. I just figured out a really sweet way to do it without lifting a finger.
You can run commands though SSH by using ' around the commands.
Pages

