Linux permissions explained
Linux based systems are the most secure operating systems in existence. one of the reason for this is the way they handle permissions. Permissions are rules that describe what can be done with a file and by who. Permissions are also one of the biggest mysteries to many new users as well as the cause of many problems. Working with permissions is not difficult, its honestly quite easy once you understand the basics behind why it works the way it does.
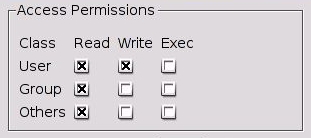 There are 3 basic permissions in Linux. Read, Write, and Execute. These permissions apply to three sections. These sections are User, Group, and Other. The User section is the owner of the file. This ownership states who this file belongs to. The Group section is the collection of users that can use the file. Finally the other section describes special permissions given to unauthenticated or anonymous users.
There are 3 basic permissions in Linux. Read, Write, and Execute. These permissions apply to three sections. These sections are User, Group, and Other. The User section is the owner of the file. This ownership states who this file belongs to. The Group section is the collection of users that can use the file. Finally the other section describes special permissions given to unauthenticated or anonymous users.
This seams complicated but honestly it's quite simple. Lets assume you have a small team of people that need to have access to a special document. However, you want to be the only person that can change this document. You also want this document to stay secret and only allow your small team access to it. For this example we will call your team "TeamA" and your user name will be "User1". First we will change the group ownership to "TeamA". We will then set the user permissions to read and write and the group permissions to read. Finally we will change the other permissions to nothing. That's all there is to it. Now the owner, you, can read and modify the file, the other team members in your group can only read the file, and all other access from other users has been taken away.
These rules do not just apply to documents, they also apply to applications. Linux is truly a multi user operating system. The user files are completely isolated from the programs and operating system. This is in part done with permissions as well as physical location. For instance when you run Firefox the executable is marked as read and execute for the user group but the executable itself is owned by root with read, write, and execute permissions. This means that anyone in the user group can read and execute the file but only root can change it.
This can be used to restrict access to applications in environments where you need that control. For example, lets assume that you only want specific people to have access to Firefox. The process required to do this is quite simple. First you have to create a new group, we will call it "surfing". Second we will change the group ownership of the Firefox executable to the group we just created, "surfing". Third we will change the permissions in the group section of the Firefox executable to read and execute. Then only add the people you want using Firefox to the "surfing" group. Now when anyone not in the surfing group tries to run Firefox they will be denied permission. This would be a great way to stop employees from spending all day on Facebook.
The benefits to restricting access to files and programs does not just stop here. There is a good reason why Linux is so secure and it is in a big part to permissions that make it possible. All data and settings for a user are stored in the users home directory (/home/"user"). Its in this directory that a user for the most part has full control. The rest of the system is isolated from the user by permissions. Since we have already been using Firefox as an example lets continue. All the data, settings and cache for Firefox is stored in the user’s home directory but the application itself is located in the /usr/ directory. By default the executable is only given read permissions to the users, only root has write permissions. By doing it this way the application can only be updated or changed by the root account but can be used by everyone. Therefor without root access the file cannot be changed. This would stop a virus from changing the actual executable to something malicious.
Permissions protect files and executables outside of the users home directory from being modified by the user or a malicious attack. Permissions also protect files within the users home directory from access and modification from other users. However, this would not stop a virus from just creating a fake / malicious executable in the users home directory. Still this could only effect the user and not the whole system without root access. As a protection from this there is another part of the Linux system that controls default permissions for new files, its called umask. Umask handles default permissions for files added to the system. This gives the files baseline permissions to start from. By default the files are normally owned by the user that downloaded them and part of the user group. These files have basic read and write permissions for group and user as well as read permissions for other, or guest. In order to execute a binary file it’s execute permissions must be added, otherwise the system treats the executable as a regular file and does not even attempt to execute it.
To explain umask in more detail we will have to explain permissions in a little more detail. To start with Linux systems use numbers to associate permissions. As an example the permissions 777 would equal (rwx, rwx, rwx) or (Read, Write, and eXecute) for all sections user, group, and other. Most files in Linux have default permissions of 644 (rw_, r__, r__) or (Read, Write) for user and (Read) for group and other. The way this works is the first number signifies the user permissions, the second number signifies the group permissions, and the last number signifies the other permissions. The number 4 represents read only permissions, the number 6 represents read and write permissions and the number 7 represents read, write, and execute permissions.
Here is a chart of permissions with their number representation.
| 0 | Nothing |
| 1 | Execute |
| 2 | Write |
| 3 | Write, Execute |
| 4 | Read |
| 5 | Read, Execute |
| 6 | Read, Write |
| 7 | Read, Write, Execute |
As you may probably see permissions in Linux are nothing but a math problem. If you would like a file to have read and write permissions you would just add the values of both read and write up. Read = 4 and Write = 2, 4+2=6 and Read and Write = 6. These number representations of permissions in Linux are called a files mask. No file can exist in Linux without a mask, it's absolutely required. This is where umask comes in.
Just as giving a file permissions is nothing short of a math problem umask does this by taking away from the mask. By default a new file on a Linux system can have a maximum default mask of 666 (rw_, rw_, rw_) or Read and Write for all sections. Linux will not allow execute permissions by default so if execute permissions are required it has to be manually set. Most Linux systems have a default umask of 022. The way this works is you take the maximum allowed mask of 666 and subtract the umask value from it making 644 (rw_,r__,r__). If you would like each new file to have write permissions for the user and group you would change the umask to 002. This would give you a default mask of 664 (rw_, rw_, r__). This goes for files that are downloaded or created on the computer.
Changing permissions from the terminal
To put all this information to use you need to know how to actually change file permissions. The best and easiest way to do this is from a terminal. There are three commands that you will use most of the time and those are chmod, chown, and chgrp. Each of these commands have a different purpose.
CHMOD
CHMOD is the command that's used to change the actual mask value of a file. If you have a file with a mask of 644 (rw_,r__,r__) and you would like to give the files group write permissions the command would be.
| chmod 664 filename |
filename being the path and name of the file you wish to modify the mask to.
664 being (rw_, rw_, r__)
CHOWN
CHOWN is the command you would use to change the ownership of a file. To use CHOWN you have to have root permissions. If you have a file that's owned by user1 and you would like it to be owned by user2 then the command would be.
| chown user2 filename |
user2 being the user you would like to own the file.
filename being the path and file name of the file you wish to modify.
CHGRP
CHGRP is the command used to change the group ownership of a file. You must be part of the group that you wish to change the group ownership to. If you want a file to be part of the "newgroup" group then the command would be.
| chgrp newgroup filename |
newgroup being the name of the group you would like the ownership group of the file to belong to.
filename being the path and name of the file you wish to modify.
In closing this system of permissions may seem complicated at first. However, this system is one of the critical parts that makes Linux so secure. There are many possibilities to what can be done with permissions in Linux. There are also many things that can go wrong. If a required program has incorrect permissions it could make a system not useable or at very least make a program unable to execute properly. So next time something does not work the way it should I suggest checking file permissions before spending time following other avenues. A huge problem may sometimes actually be just the wrong permissions.
Share

